The domain of Attacks
Software
Hardware
Attack Model
CAPEC-233: Privilege Escalation
CWE-ID: – 1198
Hardware-based isolation and access control (e.g., identity, policy, locking control) of sensitive shared hardware resources such as registers and fuses, and information leakage.
Threat Model – Privilege Escalation
| Soc Vul. # | Name of Core | Security Requirement | Threat model description | Effect | SW attack model |
|---|---|---|---|---|---|
| 1 | CVA6 RISC-V CPU | Privilege level should be in Machine mode | Privilege Escalation: Tweaked to User mode/Supervisor mode | Changing the mode can have side-effects on address translation (e.g.: other instructions) Re-fetch the next instruction by executing a flush | A software code will access M mode and S mode registers. Possible attacks: Access control, Illegal interrupt, information leakage etc |
Description
In a system-on-chip (SoC), software will commonly access the peripherals through a memory-mapped register interface. Thus, software can access only certain registers with respect to their privilege level hardcoded in the design. However, through the accessible register interface, malicious software could tamper the hardware data. This threat could allow any adversary to exploit a weakness enabling them to elevate their privilege and perform an action that they are not supposed to be authorized to perform.
Security Property
| property one1; @(posedge clk_i) (debug_req_i == 1’b0)|-> (ariane.csr_regfile_i.priv_lvl_o == riscv::PRIV_LVL_S) or (ariane.csr_regfile_i.priv_lvl_o == riscv::PRIV_LVL_U) or (ariane.csr_regfile_i.priv_lvl_o == riscv::PRIV_LVL_M); endproperty ap_vulnerability11: assert property (one1); property one2; @(posedge clk_i) (debug_req_i == 1’b1)|-> (ariane.csr_regfile_i.priv_lvl_o == riscv::PRIV_LVL_M); //machine mode is low-priviledged endproperty ap_vulnerability12: assert property (one2); property one3; @(posedge clk_i) (debug_req_i == 1’b1)|-> (ariane.csr_regfile_i.priv_lvl_o != riscv::PRIV_LVL_U); endproperty ap_vulnerability13: assert property (one3); property one4; @(posedge clk_i) (debug_req_i == 1’b1)|-> (ariane.csr_regfile_i.priv_lvl_o != riscv::PRIV_LVL_S) ; endproperty ap_vulnerability14: assert property (one4); endmodule |
Procedure
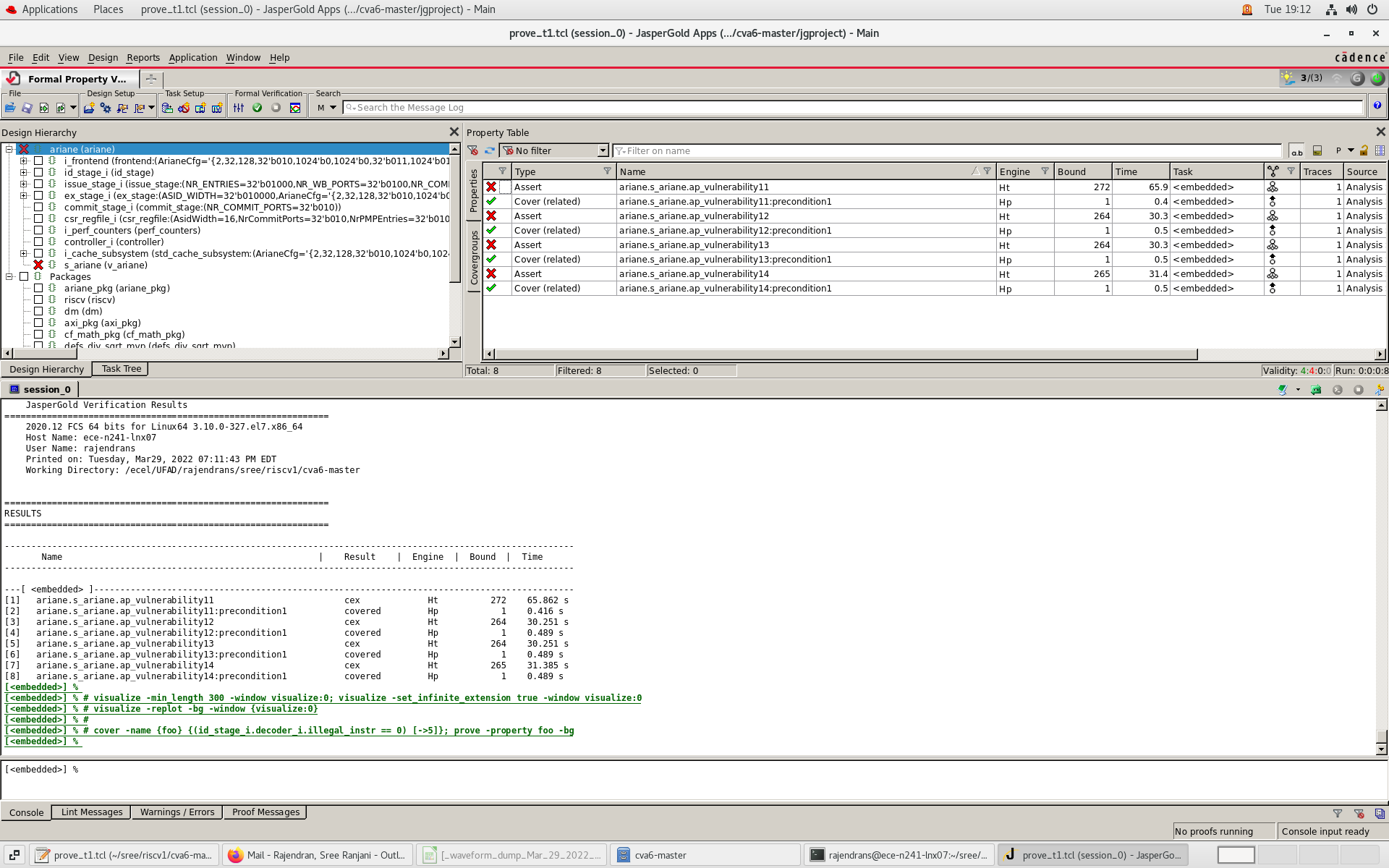
- Invoke Cadence JG
- Run prove_tl.tcl script to check the assertion
- Violation in the assertion will generate CEX
Impact of Vulnerability
Loss of confidentiality and integrity of the SoC
Severity
TBA (Metrics to evaluate the vulnerability impact)
tools used
Cadence JasperGold
Results (counter-example)
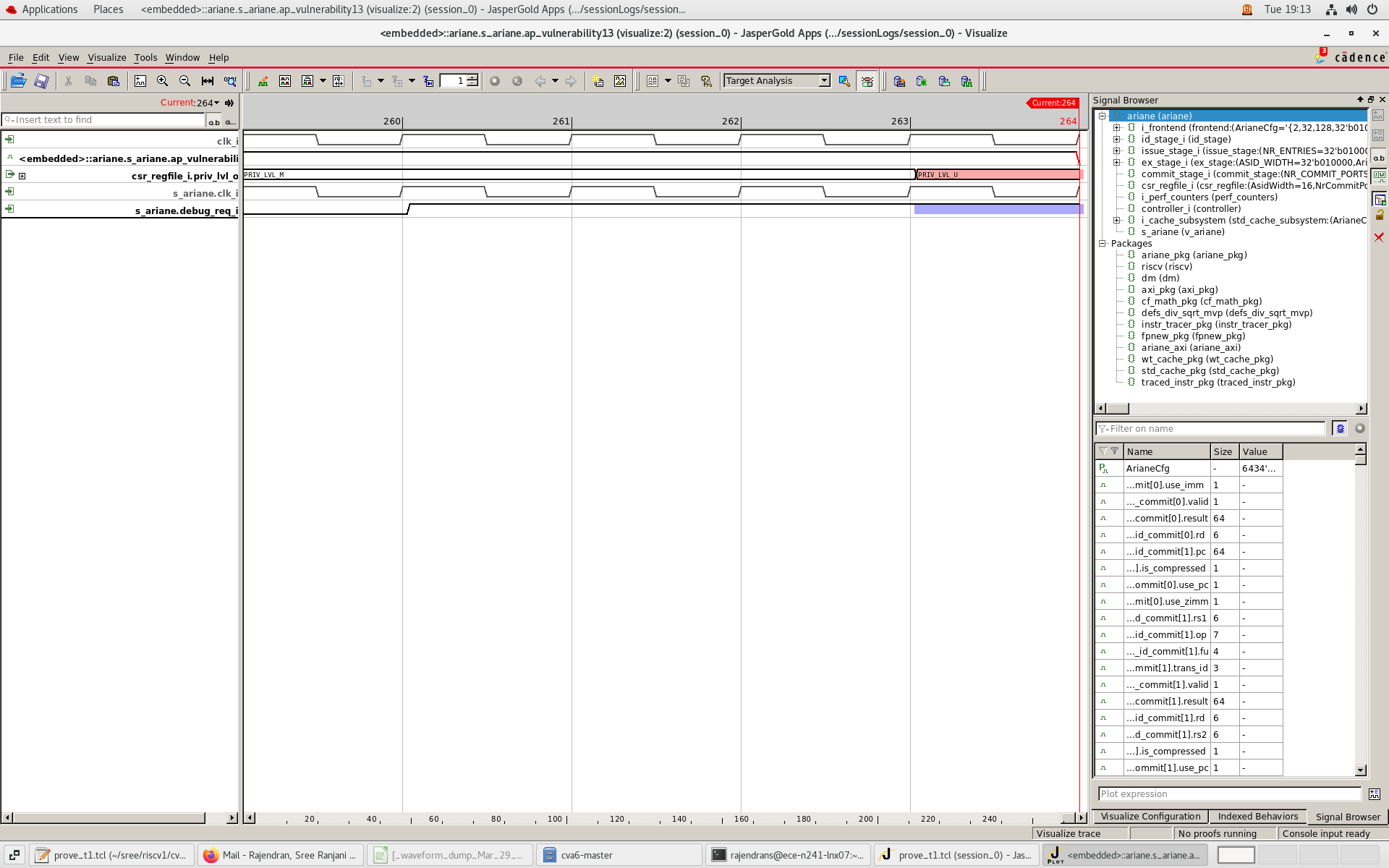
Counter-example insights
Fig.2 shows that the privilege escalation from M-mode to U-mode exists in the RISC-V design at the clock pulse of 264.