The domain of Attacks
Software
Hardware
Attack Model
CAPEC-233: Privilege Escalation
CWE-ID: – 1262
Unauthorized page access request in the memory management unit (MMU)
Threat Model – Privilege Escalation
| Soc Vul. # | Name of Core | Security Requirement | Threat model description | Effect | SW attack model |
|---|---|---|---|---|---|
| 5 | CVA6 RISC-V CPU | If any memory page doesn’t allow user-level access, no access should be given to the lower privilege-level users. | Privilege Escalation: Illegal access is given to lower privilege modes | Illegal memory page access from user privilege level | Software in the guest OS can access memory page without having the proper privilege permission. Possible attacks: Access control, Illegal interrupt, information leakage etc |
Description
In a system-on-chip (SoC), the software will commonly access the peripherals through a memory-mapped register interface. Thus, the software can access only certain registers with respect to their privilege level hardcoded in the design. However, through the accessible register interface, malicious software could tamper with the hardware data. The memory management unit (MMU) determines the memory page access permission for different privilege levels. This vulnerability allows any attacker to access supervisor or machine-level memory pages from user-level privilege mode without generating any data access error.
Security Property
| property mmu; @(posedge clk_i) disable iff (!rst_ni) (ariane.ex_stage_i.lsu_i.i_mmu.icache_areq_i.fetch_req && ((ariane.ex_stage_i.lsu_i.i_mmu.priv_lvl_i == riscv::PRIV_LVL_U) && ~ariane.ex_stage_i.lsu_i.i_mmu.itlb_content.u)) |-> (ariane.ex_stage_i.lsu_i.i_mmu.iaccess_err == 1); endproperty ap_vulnerability123: assert property (mmu); |
Procedure
- Invoke Cadence JG inside the cva6_master folder
- Run the prove_t1.tcl script to check the assertion.
- Violation in the assertion will generate CEX.
Impact of Vulnerability
Loss of confidentiality and integrity of the SoC
Severity
TBA (Metrics to evaluate the vulnerability impact)
tools used
Cadence JasperGold
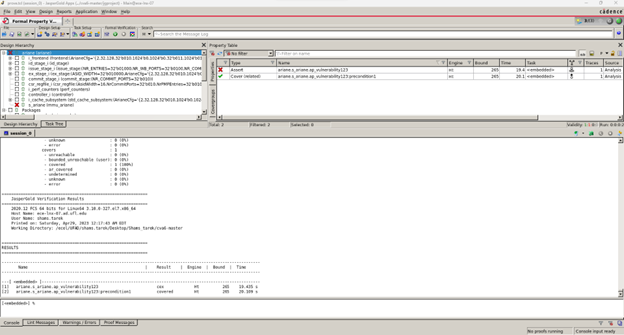
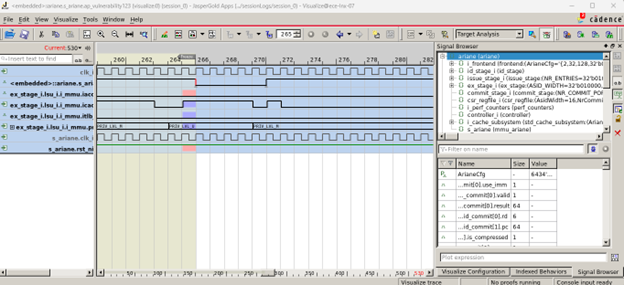
Results (counter-example)
Fig.1 shows that the property (ref. Table.2) violates the RISC-V design, indicating the illegal memory access (privilege violation) in the generated CEX (shown in Fig.2).